ACS Right line
Solution for Issuing Banks and TPP

ACS Right line is certified in EMVCo, MIR, VISA, Mastercard and Union Pay International payment systems.



ACS (Access Control Server) is the issuer’s server responsible for interacting with the DS server of the payment system, with the issuer’s decision–making services and the cardholder. The development belongs to Wright Line LLC, which is the copyright holder of RID, and is listed in the Russian software registry (Registry entry No. 14752 dated 09/05/2022). ACS is one of the components of the 3-D Secure infrastructure.
The ACS solution is included in the registry of domestic software, and also has its own control panel with an intuitive interface and convenient settings for risk rules and black/white lists. To calculate the cost of the solution, you need to create an application on the website.
Solution
possibilities
Interaction with decision-making services of the issuing bank
Exchange of messages with the payment system server (DS)
Interaction with the card owner in a Challenge scenario
Formation of a cryptogram (AV)
Advantages of ACS Right line solution

Supports 3DS v.1 (Visa/MS) and EMV 3DS v.2 (MIR)
Included in the unified register of Russian computer programs and databases
Possibility of horizontal scaling
ACS Right line solution is technologically compatible with PostgreSQL
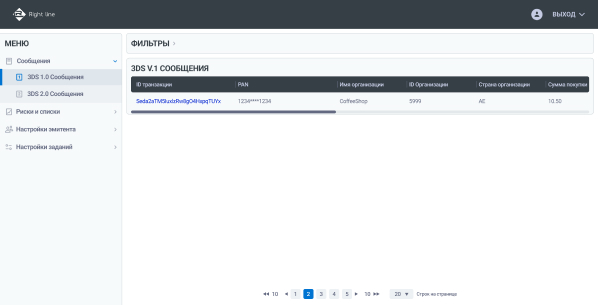
Convenient control panel for viewing 3DS messages
Characteristics of ACS Right line
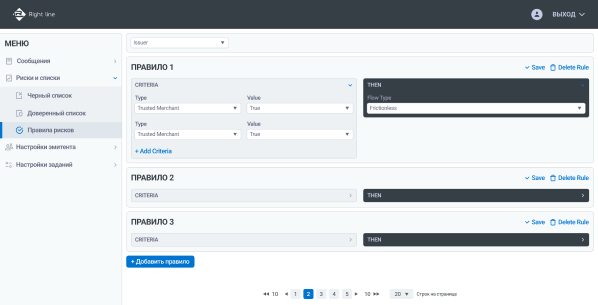
Internal scoring
Has its own internal decision-making service capable of authentication through the Frictionless or Challenge script
Certification
Certified by NSPK and supports versions 1.0.2 (Visa, MS), 2.1.0 and 2.2.0 (Mir) of the 3-D Secure protocol. Has a certificate of technological compatibility with Postgres Pro Standard 13, 14, 15
On-us support
Supports the processing scheme for on-us transactions within the bank circuit, without using Directory Servers of payment systems
Integrations
Integrates with any internal bank systems (CRM, Mobile Bank, FMS, Notification Gate) and external systems (Mastercard Identity Check and others) for authentication
Scalability
Solution can work both as a single node and in balanced and managed cluster mode from several nodes 24/7
Safety
Ability to use multiple HSMs at the same time
Scoring
Has support for processing riscScoring SPR (NSPK) values, which allows you to increase the number of Frictionless authentications
Risk-based
authentication
The user authorization method is determined based on the risk assessment in the authentication request.
Three implementation options:
Built-in risk-based authentication (RBA) engine
Risk assessment is carried out based on the rules and parameters specified in the risk model
Risk assessment by an external system
The ACS transmits the data received in the authentication request to the external system and in response receives the client authentication method
Hybrid model
Uses an inbuilt RBA engine with calls to external systems to check individual risk rules

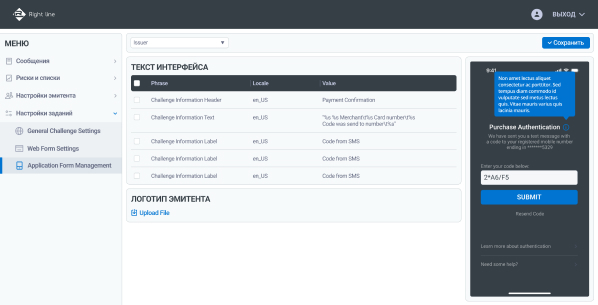
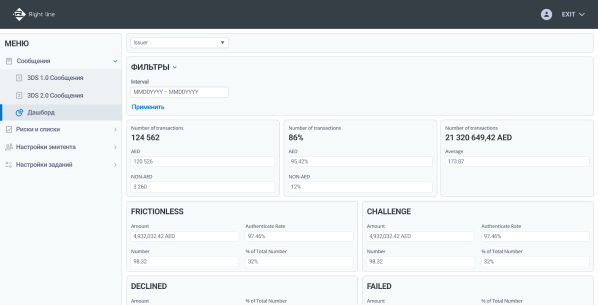
UI. Control panel
Functionality of the ACS Right line control panel